
On Saturday night Iranian hackers, known as the "Promised Revenge," hacked the Rimon Internet Provider, which provides Internet filtering services for the religious and haredi sectors.
The incident began around 11:30 p.m., since when many customers reported severe disruptions in service, to the point of partial or complete disconnection from the network.
Internet Rimon published the following response this morning: "On August 23, 2025, we detected an attack from a hostile entity. Immediately upon discovery of the incident, we took action to block the attack and currently, after extensive activity by the company's technology teams and other leading entities in Israel, we are reconnecting our customers to the service. Some customers may still experience difficulties connecting to the Internet and disruptions in filtering services. We are doing our utmost to restore the service to its continuous and full form. We thank our customers for their understanding and trust in the company's services. Rimon Internet Management."
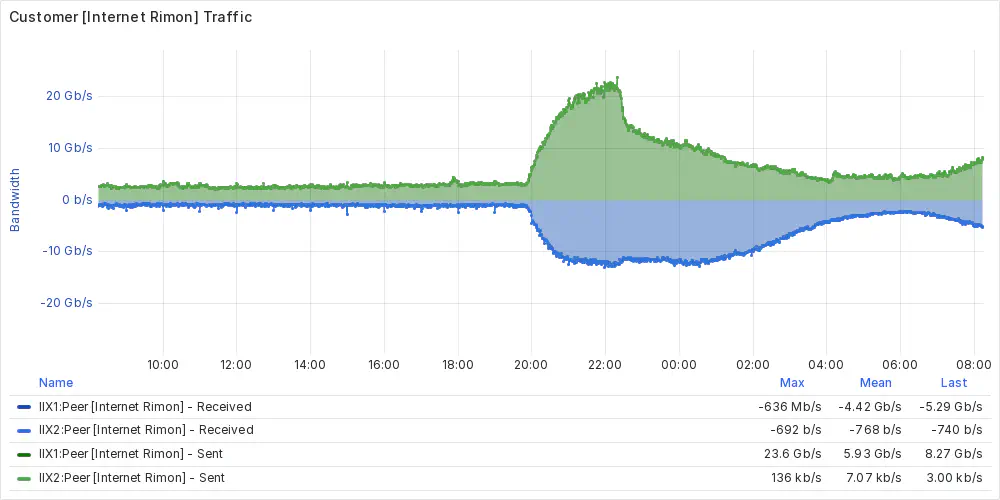
Rimon IIX (the Israeli Internet Exchange)’s communication graph show a decrease in traffic around the time of the hack, but not a total halt. This morning, some of the provider's customers seem to have internet, but not all.
At the same time, the hackers released a video in which they claimed in real time to hack Rimon computers, while disabling servers and deleting internal infrastructure. The group has not yet presented evidence of information theft, but claims that it has managed to obtain sensitive information from the company's internal network. According to Rimon, "at this stage there are no indications that personal customer information has been leaked."
How does Rimon Internet filtering work and what is the risk of a hack?
Rimon Internet filters content by routing all traffic through its servers, acting as an Internet provider with full oversight. Using a legitimate MITM (Man-in-the-Middle) method, it decrypts HTTPS traffic, scans it by user rules, blocks unwanted content, and then restores browsing.
This gives the company access to sensitive data: site addresses, page content, and even login details. A breach could expose not only credentials but also personal information such as preferences, filtered content, and correspondence.
Currently, Rimon’s services are down, with support limited to a recorded line (*8900) and Facebook updates. Its websites, including subsidiaries Etrog and NetFiber, are also offline. Some customers report partial recovery, but the incident remains unresolved.